
Accelerate secure software delivery and reduce development costs
QuarkLink™ is a device SDK and cloud platform that lets teams building embedded software for connected devices reduce time, cost and risk of implementing security by design.
Development teams are spending 35% of their project time re-inventing the security wheel
Embedded IoT developers are burdened by complex, time-consuming security tasks. Different MCU and CPU types demand specialised security development, forcing repeated implementation of features like secure boot and secure FOTA with low level libraries. This process is not only resource-intensive and error-prone, but also fragments development efforts, delays go-to-market, and complicates ongoing support.
The included SDKs are part of QuarkLink’s integrated functionality that gives developers a powerful toolkit upon which to build security features.
Remove Complexity
Eliminate the headaches of secure boot, authentication, and secrets management. Simplify security so your team can focus on core product innovation
Faster Speed-to-Market
Stop re-inventing the wheel and get to market faster by building with proven security building blocks and a powerful CLI. Cross MCU, CPU and MPU support takes the risk out of porting to new architectures
Free Up Your Engineers
Reduce the burden on your embedded specialists. Focus R&D on high-value features
Fast, Compliant Development
Accelerate development whilst ensure compliance in secure-by-design environments
Eliminate OTA Update Risk
Ensure reliable and error-free updates with integrated secure OTA
Eliminate Certificate Misuse
Protect against unauthorised access and accidental misuse with automated, secure certificate & key management that integrates into the development workflow
Explore QuarkLink™ (each module can be used independently)
Provisioning & Secure Boot
Automate device identity, key generation, and first-boot security.
OTA Updates & Service Onboarding
Connect devices to cloud platforms and push signed firmware updates.
Fleet & Certificate Management
Manage certificates, lifecycle events, and secure updates at scale.
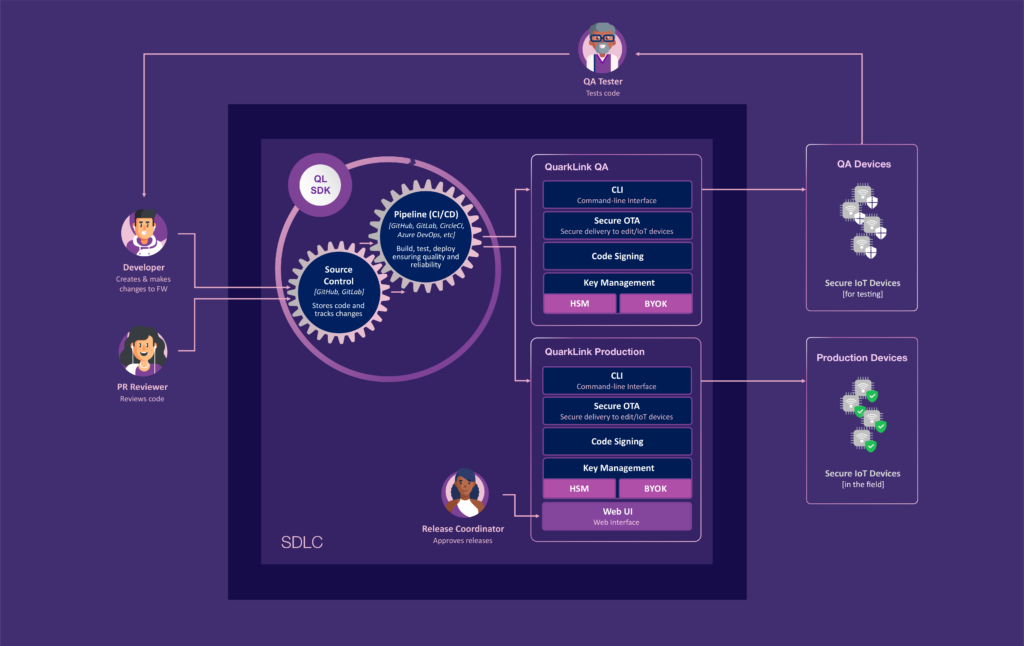
Software development lifecycle integration (SDLC, CI/CD)
Whatever DevOps tooling you use (e.g. GitHub, GitLab, Jenkins, etc) QuarkLink™ integrates into your team’s existing software development lifecycle (SDLC, CI/CD).
Accelerate secure software delivery and reduce development costs. Allow your teams to focus on creating value through their code and rely on QuarkLink™ to take care of device security.
Key and certificate management (PKI/CLM)
QuarkLink™ takes care of securely storing keys and managing certificates, automating their creation, revocation, renewal, and reissue.
By centralizing and automating the management of keys and certificates, organizations can enhance visibility, reduce the risk of errors, and prevent outages caused by expired or compromised certificates.
Supported Devices & Platforms
QuarkLink™ works with any connected IoT device, from powerful SoCs running Linux to bare metal resource constrained MCUs.
Choose from common Linux distributions including Yocto, Debian, Ubuntu, Raspberry Pi OS, and popular hardware suppliers like NVIDIA, NXP, Renesas, ST Micro, and Microchip.
On-device security features (e.g. secure boot, flash encryption)
Protect devices against malicious software attacks at boot-time by ensuring that only trusted software, verified by a digital signature, is allowed to run.
Stop attackers taking over the device to steal sensitive data, launch distributed denial-of-service (DDoS) attacks, or use the device as a gateway to infiltrate connected networks.
On-device key generation & storage
QuarkLink™ implements on-device key generation so device keys and identities are unique and never exposed during transmission or shared outside the device.
Reduce the risk of keys being compromised leading to device impersonation, decryption of sensitive data, or execution of unauthorized actions. You never have to share private keys by email or USB again!
Code signing & secure over-the-air updates (OTA)
Code signing/encryption is automated and signing keys are managed securely by QuarkLink™. Deployment of code is made easy with over-the-air updates (OTA).
Prevent the execution of unauthorized or tampered software and reduce the manual effort, and potential human error, in your development teams.
Onboarding to cloud services (e.g. IoT hubs, message brokers)
QuarkLink™ securely connects devices to all major IoT hubs, including AWS, Azure, and other MQTT or message brokers, and is equally able to work with private clouds or other services.
Unique device identities and mutual TLS ensure that both the device and the cloud service authenticate each other, reducing the risk of unauthorized access by cloned devices.
Device lifecycle management
QuarkLink™ can monitor a device’s firmware integrity to detect compromises or cyberattacks. In such a case, it can unlink a device from its system, disconnect it from servers and revoke its keys. And if a device changes ownership, it can be re-onboarded easily.
QuarkLink™ Device SDK
Provides secure boot, authentication, and provisioning with minimal code and no cryptography expertise required. Works across multiple device platforms, reducing the need for platform-specific development.
QuarkLink™ Cloud
Centralized platform for managing device identities, performing firmware updates, and monitoring security in real-time at scale.
QuarkLink™ CLI
Automates scalable and secure device provisioning, key management, and OTA updates into CI/CD pipelines and production workflows.
Accelerate compliance with the Cyber Resilience Act (CRA)
The EU Cyber Resilience Act (CRA) introduces mandatory security requirements for all connected products sold in Europe. QuarkLink™ has been independently evaluated by leading cybersecurity consultancy cetome, with findings confirming that it significantly supports CRA compliance.
Highlights from the independent assessment:
- Secure-by-default configuration: ⭐ Excellent
- Secure firmware updates (OTA): ⭐ Excellent
- Data integrity: ⭐ Excellent
- Secure-by-design support: ✅ Good
- Access control: ✅ Good
- Data confidentiality: ✅ Good
QuarkLink provides secure boot, certificate management, and OTA update features which are key to building secure-by-design products ready for CE Marking and CRA compliance.
Download QuarkLink CRA Assessment
“Implementing secure boot is complex, it elevates the design complexity, it requires significant effort to verify multiple use cases.”
– VP Engineering, Medical Devices
Will QuarkLink™ work for me?
Q. I don’t see my hardware listed, do you support it?
We support all major embedded platforms including MCU’s running bare metal, popular RTOS, and devices running Linux. We currently have integration guides for devices from NXP, Renesas, Microchip, ST, etc. If we don’t currently have an integration guide for your device we’d love to talk to you and see if we can add one.
Q. Are my private keys locked-in with QuarkLink?
No, we support a variety of HSMs (including any that use the PKCS11 standard) and as part of the QuarkLink set-up you define which HSM you would like to use
Ready to get started?
QuarkLink Ignite™ is a completely free version of our SaaS product that allows you to experience the full power of QuarkLink™
Try for free Book a demo Contact sales

