What is Matter?
By Amit Deo, PhD, and Senior Cryptography Researcher at Crypto Quantique. A brief overview of the Matter communications standard and the security-centric aspects of the device onboarding process.
In this blog post, we look at one of the most promising solutions to the fragmentation problem in the IoT industry – the Matter communication standard. Along the way, we will give a brief overview of the standard and the security-centric aspects of the “device onboarding” process.
The IoT fragmentation problem
Suppose I have a system of sensor devices in my home that I bought a year ago from manufacturer A. Suppose also that manufacturer B has invented new and improved sensor technology and I want to add these to my current sensor system. It may well be the case that the new sensors cannot interact with the old ones since they are built by a different manufacturer. As a consumer, I have two options: the first is to buy more of the old sensors and the second is to scrap my current system and buy a complete set of new sensors. The first option may be cheaper but denies me access to the latest technology whereas the second may be prohibitively costly. This situation is common in the IoT industry as fresh players find niches and make technological advancements on what is available today. The lack of interoperability of devices produced by different manufacturers/designers is known as the fragmentation problem.
What is Matter?
Matter is a communication standard designed by the CSA (Connectivity Standards Alliance) to solve the fragmentation issue in the IoT industry. The CSA is a community of various members including technology giants such as Amazon, Apple, and Google. The collaborative nature of the CSA will no doubt encourage the adoption of standards as major players will have had their say on how the standard was designed.
The overall idea is that any two devices that use the Matter standard should be able to easily communicate, providing the customer with the desired connected service or application. To get a better feel of what Matter aims to do, it is useful to recall its original name – Project CHIP. This acronym stands for “Connected Home Over IP” – suggesting a communication standard that allows all smart devices within a home to communicate seamlessly over an IP network. With widespread adoption, end users will no longer be locked into buying products from a single manufacturer with interoperability being an expected norm. Furthermore, the startup time/costs of newer manufacturers will be reduced as they can use open-source Matter implementations as a de facto standard communication protocol. Overall, Matter is expected to lead to a better consumer experience and faster development of innovative IoT technologies.
Matter dictates the various aspects of setting up and operating a home network of IoT devices. Specifically, it describes the method by which new devices can be onboarded i.e., enrolled as a trusted device as well as the methods by which enrolled devices can communicate in a confidential and authenticated manner.
What certificates does Matter use?
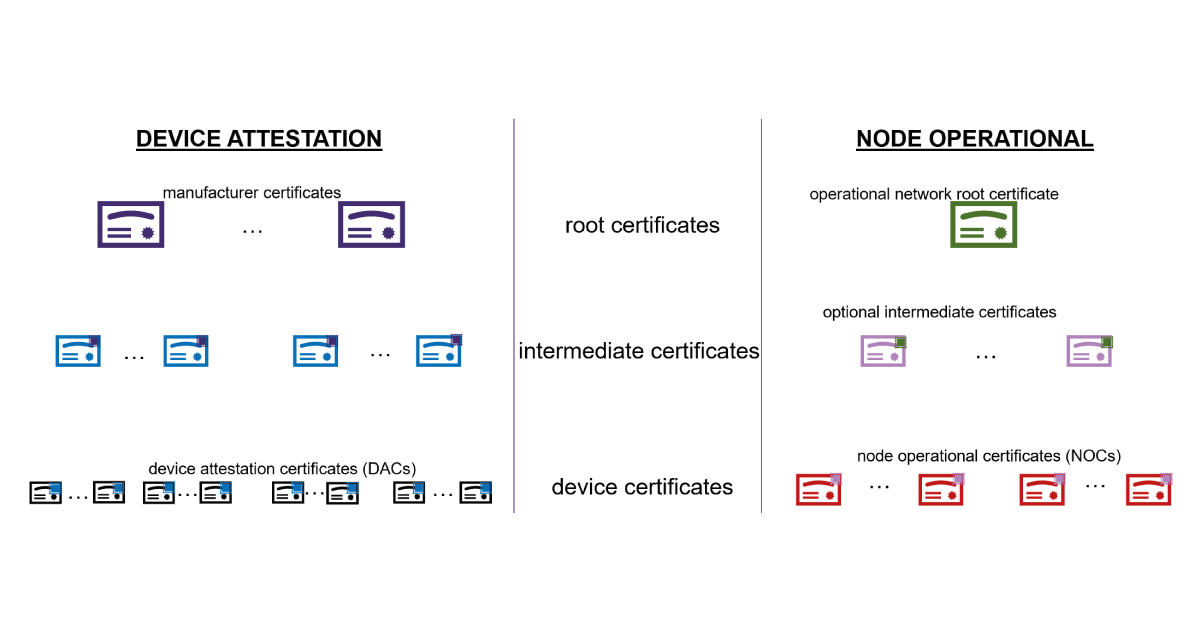
To provide authentication of Matter devices, public key infrastructures are used. There are two main types of public key certificates used in the Matter standard: device attestation certificates (DACs) and node operational certificates (NOCs). The former serves as a manufacturer’s stamp of approval that a device has certain characteristics i.e., some device was genuinely manufactured by a certain manufacturer and uses certain hardware. The latter proves that a device is permitted to be part of a home operational network.
Certification Type: Device Attestation (DAC)
Purpose: Attest to device-specific information e.g., manufacturer ID, device model, firmware
Certificate Authority: Manufacturer
Certification Type: Node Operational (NOC)
Purpose: Attest to the fact that the device is known and trusted by the network administrator
Certificate Authority: Home Network Administrator
A general requirement of a public key certificate is that it should be signed or “rubber-stamped” by some trusted entity known as a certificate authority. In practice, the certificate authority does not directly sign an end device certificate. Instead, it is signed by an intermediary who possesses a certificate signed by the certificate authority. Then to trust a device’s certificate, one must check that the intermediary’s certificate is signed by the root certificate authority and that the intermediary signs the end device certificate. This hierarchy of certificates is depicted in Figure 1. For more information on general principles behind public key infrastructure, or PKI, see PKI Explained | Public Key Infrastructure (thecyphere.com).
How does Matter onboarding work?
Device enrolment into a home network is known as onboarding. The simplified high-level process of Matter onboarding is given in Figure 2. In the picture, arrows within the existing home/operational network signify lines of communication between the various devices within the network. IoT devices can speak to admin devices, the Wi-Fi router, and even other Matter-enabled devices. Importantly, for all enrolled devices in the existing operational network, the communication is encrypted and authenticated. Another crucial point is that the commissioner device and the network administrator may be the same entity, but the Matter specification treats them as separate for generality. Finally, to understand the picture, we make the following assumptions:
- If a device performs device attestation, it already possesses a DAC
- A device can produce a password (the exact method by which this password is produced is out of the scope of Matter)
- The device is near the home network/commissioner device
- The commissioner device knows and trusts all possible DAC root certificates
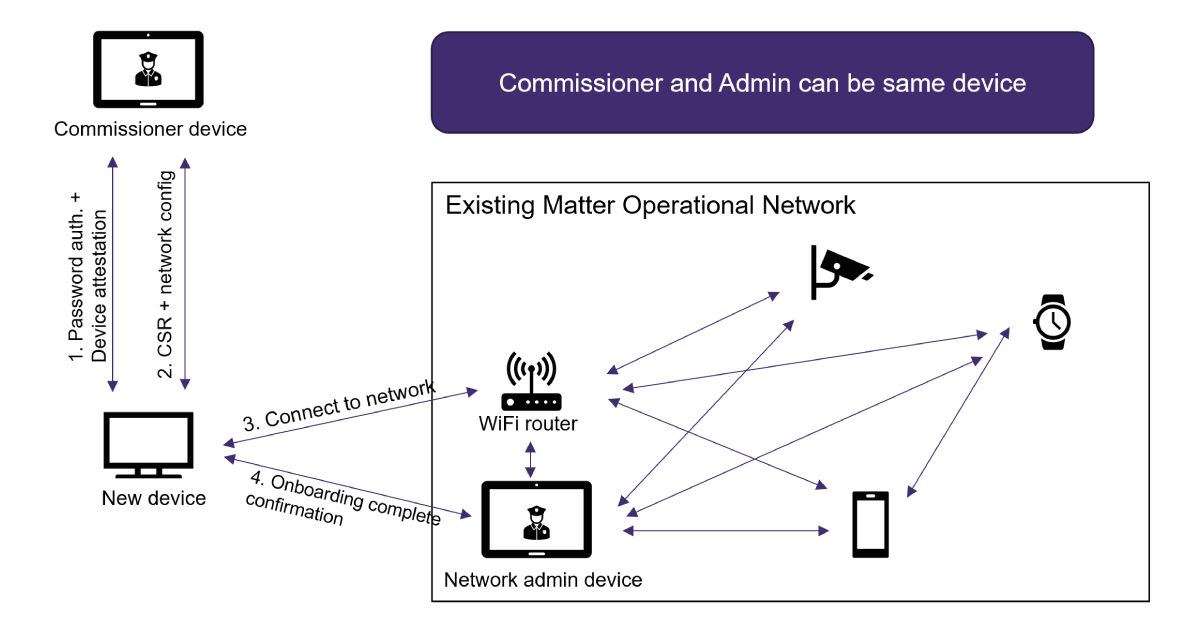
Elaborating on the picture, we have the following steps and descriptions.
- Password Authentication + Device Attestation:
- The device creates a password and transfers it, out of band, to the commissioner device. This can be done by creating and scanning a QR code if the device has a screen, and the commissioning device has a camera. Alternatively, the password may be transferred via a file.
- The device and commissioner use a symmetric password-authenticated key exchange (sPAKE). To get an idea of how sPAKE works, this is a really clearly written blog post on the subject. Using sPAKE lets the commissioner know that it is speaking to the device that created the password. After this, the keys exchanged provide subsequent encryption and authentication.
- The device and commissioner perform device attestation using the DAC on the device. This comprises of the device proving that it owns the certificate and the commissioner checking the validity of the certificate concerning a manufacturer certificate authority. To prove that it owns a certificate, a device must produce a fresh signature that is consistent with the public key on the certificate. The data signed includes a random number/nonce from the commissioner and device-specific information e.g., a firmware version.
- Certificate Signing Request (CSR) and Network Configuration: The device requests a NOC to allow it to authenticate as a trusted device within the home operational network. This is done using a standard secure CSR mechanism. In addition to the NOC, it receives important network configuration information (such as Wi-Fi SSID, password, network administrator IP address, network root certificate, etc.).
- Connect to Network: The device uses the network configuration information to make an initial connection to the home operational network.
- Onboarding Complete Confirmation: The device attempts to create an authenticated and encrypted session with the network administrator. To do this, Matter specifies a mechanism called certificate authenticated session establishment or “CASE.” This mechanism authenticates both the device and the network administrator using a protocol that mimics the IKE (internet key exchange) protocol. If the CASE mechanism is completed successfully, the administrator sends an “onboarding complete” message to the device.
Once a device has been onboarded, it is now part of the home operational network. As a result, it can make secure connections with other Matter-enabled devices. To do this, the CASE mechanism is used to derive session keys that are used to encrypt/authenticate communication. The Matter specification also provides other functionalities, such as allowing devices to communicate securely as a group of devices (rather than just a pair of devices).
A bit more on device attestation
One of the assumptions we made earlier was that the commissioner device somehow knows and trusts the DAC certificate authorities and their root certificates. The question is, why can we assume this? The answer is provided by looking at the distributed compliance ledger (Distributed Compliance Ledger (DCL) – CSA-IOT) maintained by the Connectivity Standards Alliance. This ledger provides a list of CSA-approved products, DAC root certificates, device types, and firmware versions, etc. Clearly, such a list is extremely useful for device attestation. For example, a commissioner may easily check that a new device is a CSA-approved Matter-compliant device and that the DAC is ultimately signed by the correct root certificate. It can also check (if it chooses to) that the firmware version the device sent as part of its device attestation is the latest one, rejecting the onboarding request if it is not. If the connection is refused due to out-of-date firmware the distributed compliance ledger can even be used to provide the device with a firmware update URL. To get your product on the ledger, a certification process needs to be carried out by the CSA. Unfortunately, this takes time and costs money, but in return, certification should give customers confidence in the quality of the product. At the time of writing, there were more than 4000 certified products.
In summary
Matter is a communications standard that helps reduce fragmentation in the IoT industry. Its design is centred around interoperability and simplicity, allowing users to quickly set up a fully connected home network of IoT devices. A device attestation mechanism is described which leans on the CSA’s distributed compliance ledger to check device characteristics against the latest manufacturer information. Overall, the standard should provide users with confidence that their data remains secure in various IoT applications, ensuring devices communicate in a fully authenticated and confidential manner. The Matter standard was designed collaboratively by the CSA and hopefully, this will encourage widespread adoption, allowing users to realise applications of connected IoT devices easily and flexibly in the future.
Additional resources
Whitepaper
Enabling Cloud Connectivity in Resource-Constrained IoT Devices: A Wi-Fi Module and Low-End MCU Approach
This paper explores an affordable and efficient approach to embedded device cloud connectivity using a Wi-Fi module with a low-end microcontroller unit…
Read more
Whitepaper
Hardware Root of Trust: QDID PUF & Attopsemi OTP
This whitepaper presents a simplified, secure, and ready-to-use root-of-trust solution for embedded devices by integrating Attopsemi’s I-fuse technology…
Read more
Whitepaper
QuarkLink for Industrial PCs
This white paper introduces how Crypto Quantique’s QuarkLink SaaS device security platform is used with industrial PCs running Linux.
Read more

