How to use Fingerprints for Cryptography
Amit Deo, PhD and Senior Cryptography Researcher at Crypto Quantique, explains the benefits and drawbacks of PUF authentication.
The process of authentication is extremely commonplace in the digital world. Perhaps the most frequent example is when a web-server authenticates itself to a user to give them the guarantee that the website is genuine. Another extremely standard authentication scenario is where a user wants to authenticate themselves to a remote server, say an internal company server or their bank. To perform the authentication, a user may be required to provide one or more pieces of information proving their identity such as passwords, personal information, fingerprints, video captures of themselves reading out a sequence of numbers, etc.
Similarly, the dawn of IoT introduces many scenarios where connected devices require authentication. For example, a central heating system ought to only be controlled by an authenticated thermostat. Similar to the case of user authentication, there are many options available for device authentication. In this blog post, we will look at one possible method based on Physical Unclonable Functions or ‘’PUFs’’. We will use an analogy between PUFs and biometric fingerprints to give an intuition of how we might build an authentication system from PUFs. Along the way, we will highlight the advantages of PUF-based authentication and address the challenges that arise.
What is a PUF?
A physical unclonable function or PUF is a piece of technology that can output an unpredictable and but consistent identity for itself. Usually, a PUF uses uncontrollable variations in the chip manufacturing process to provide a set of characteristics or ‘’silicon fingerprint’’ unique to each chip. To be useful, a PUF must have a method of measuring these silicon fingerprints.
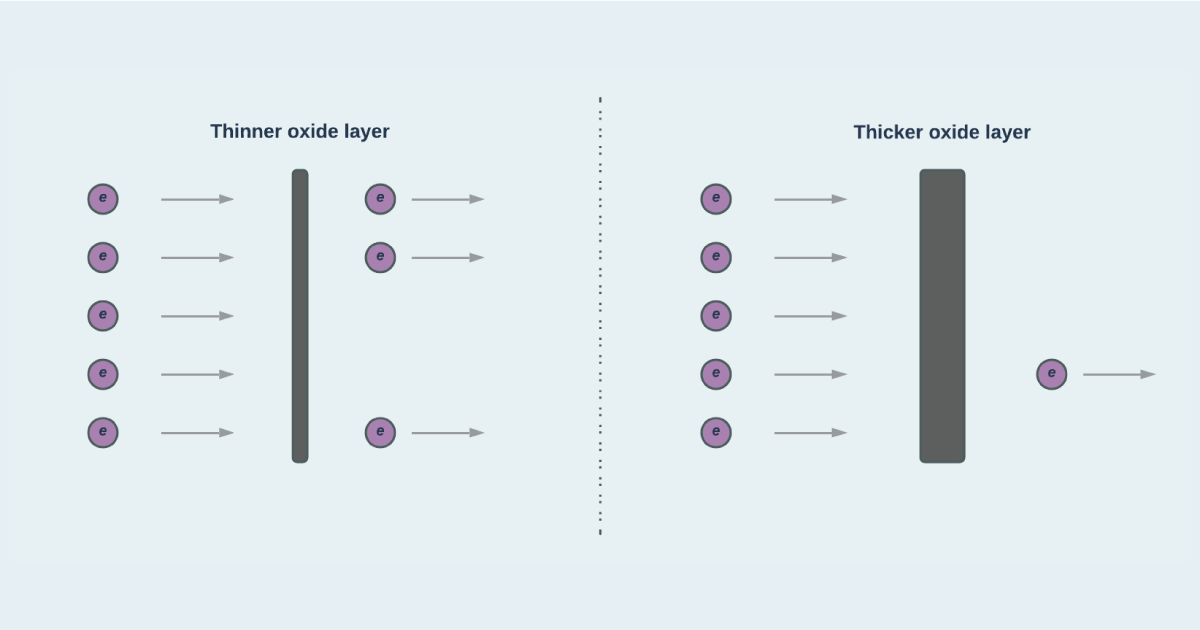
One example of a PUF is Crypto Quantique’s Quantum Driven Identity (QDIDTM). This particular PUF uses variations in oxide layer thickness across different transistors on the chip as its fingerprint. Since these thicknesses are on the scale of nanometers, a few electrons can pass through the oxide layers via an effect known as quantum tunnelling. This means that QDIDTM can ‘’measure’’ the thickness of the oxide layers by measuring the leakage current produced by quantum tunnelling. To learn more about QDIDTM, click here.
How can we use a PUF for authentication?
Biometric Fingerprint Authentication
As suggested above, a PUF provides a device with an analogue of a biometric fingerprint. We will consider a scenario where a user wants to use a fingerprint to authenticate with a remote server. To be clear, what follows is a simplified example intended to introduce main ideas/challenges for PUF-based authentication rather than a secure practical solution.
A simple biometric fingerprint-based procedure could follow these steps:
- The user enters a fingerprint image directly onto a database on the authentication server.
- To later authenticate, the user captures an image of their fingerprint using a reader (perhaps on their mobile phone) and sends the image to the authentication server.
- The server compares the image sent to the image on the database.
There are many pros and cons to this simple protocol. The first advantage is its ease of use. Specifically, a fingerprint is an inherent trait of all humans, so there is little effort required for a user to take part in the procedure. Secondly, there is no need to store fingerprints ‘’on-device’’ making them difficult to steal from a user’s device. There are also some notable cons to this simple protocol. Firstly, the authentication server initially stores and then receives copies of the user’s fingerprint. This allows the server (or any attacker that gains access to the server) to imitate the user. Secondly, any eavesdropper who can see the communication between the user and remote server can see fingerprints. Finally, variations in a fingerprint read (due to dust/finger position etc.) mean that two images of the same fingerprint are unlikely to be the same. This means user authentication may fail. We will revisit these cons in more detail in the context of PUF fingerprints next.
PUF-based ‘’fingerprint’’ authentication
We can easily translate the biometric authentication procedure with a PUF-based authentication procedure. To do this, we just have to reinterpret biometric fingerprints as PUF fingerprints. If we do this, we can write the following list of pros and cons.
Advantages:
- (A1) Ease of use: A PUF comes preinstalled on a device.
- (A2) No ‘’on-device’’ fingerprint storage: A PUF fingerprint is never stored in non-volatile device memory making it difficult to steal.
A1 and A2 are the main advantages of using a PUF over producing a device fingerprint at some intermediate stage. In the context of an IoT device without a PUF, some unique fingerprint/secret information would have to be produced and stored on a device manually. In practice, a relatively expensive solution would be to securely store the secret information using an HSM. This secret generation would have to be carried out during the manufacturing process as most IoT devices do not offer interfaces allowing end-users to do this. The entity producing and loading the fingerprints in the non-PUF scenario can therefore easily keep a copy of the fingerprints to imitate devices. This issue is overcome by A1. A second issue is that a manually produced fingerprint would have to be stored in some non-volatile memory, which is not the case when PUFs are used (see A2).
Problems:
- (P1) Server receives and stores sensitive information: The authentication server has a copy of the PUF fingerprint and receives further copies when devices authenticate, so can imitate a device.
- (P2) Eavesdroppers see fingerprints: Anyone who can see the communication between the user and remote server can see PUF fingerprints.
- (P3) PUF fingerprints are not perfectly reproducible: There are likely to be variations in PUF reads due to natural variations in the measurement process (e.g. variations in temperature or small natural variations in the leakage current for QDID)
P1 and P2 can be solved by applying standard public-key cryptography. Specifically, a device can use its PUF fingerprint as a secret key SK to derive a public key PK. The server then stores PK. To authenticate, the device proves that it knows SK by producing a signature on some random message chosen by the server. There is one major flaw with this idea though: public-key cryptography requires truly random secret keys whereas PUF fingerprints are merely unpredictable. To explain the difference between a truly random (a.k.a uniformly random) object and an unpredictable object we can use a simple example of passwords. Human-generated passwords generally have some structure/biases, so while they are unpredictable, they are not truly random. In particular, a glance at any list of the most common passwords (e.g. this list by NordPass) shows that passwords have a bias towards simple “qwerty” keyboard patterns. PUFs can be susceptible to similar (but less dramatic) structural biases meaning that while they are unpredictable, they are not truly random. This means that they should not be used directly as secret cryptographic keys.
Fundamental Challenges and Fuzzy Extractors
Following our discussion so far, we have suggested a way to address P1 and P2 by relying on public-key cryptography. However, two key challenges inherent to PUFs remain:
- Challenge 1 (Reproducibility): How do we overcome the fact that PUF fingerprints are not perfectly reproducible (i.e. how do we mitigate P3)?
- Challenge 2 (Non-uniformity): How can we use PUF fingerprints as secret keys if they are not truly random?
It is important to stress that these two challenges do not only apply to our protocol – they apply in any context where we want to use a PUF fingerprint as a reproducible and uniformly random secret key. Whether the secret key is being used for authentication or encryption is immaterial.
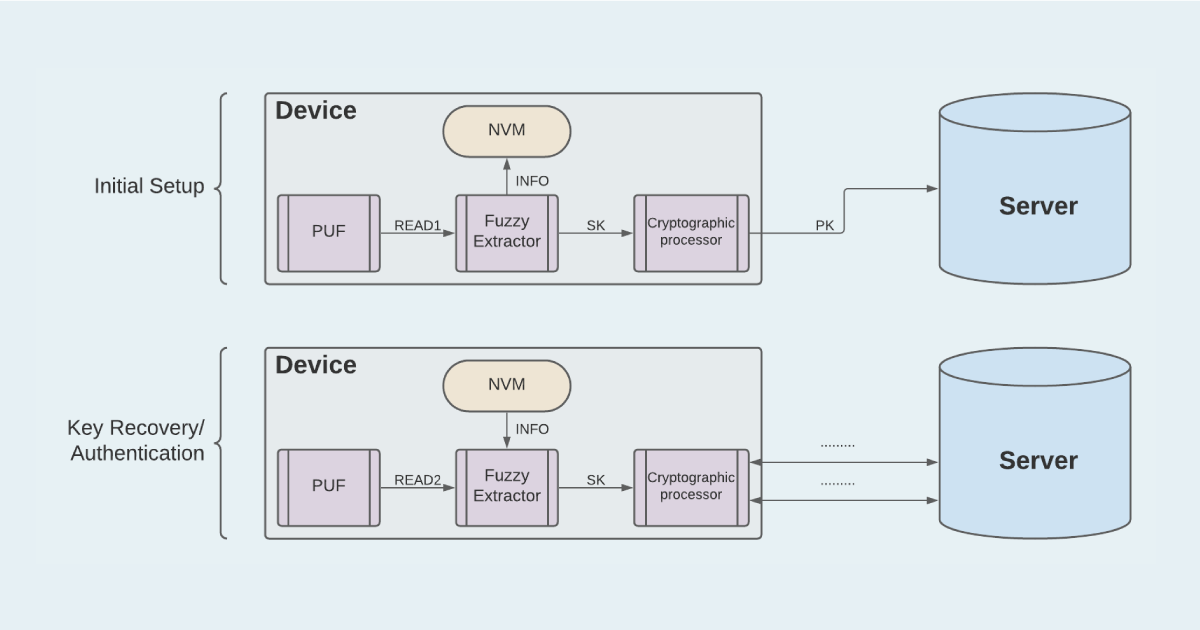
The practical solution to both of these challenges is to use an object known as a fuzzy extractor that works roughly as follows. Suppose that we take two reads of a PUF: an initial read READ1 and a subsequent read READ2. Any good PUF will have READ1 close, but not precisely equal to READ2. Then the fuzzy extractor does two things during an initial setup phase:
- It computes some extra information INFO based on READ1 that is stored permanently in device memory.
- It post-processes READ1 to produce a truly uniformly random string of bits that can be used as a secret key SK.
Later on during a key recovery phase, it uses INFO and READ2 to rederive the same secret key SK. Since INFO is stored in device memory, fuzzy extractors are designed to ensure that PUF values remain unpredictable, even to an attacker that learns INFO. A more in-depth look at what fuzzy extractors are and how they work will be the subject of a future blog post.
Conclusion
We have seen that PUFs can be used as a fundamental building block for authentication protocols, using the analogy of biometric fingerprint authentication. The very simple base authentication protocol that we discussed showed the pros of PUF based authentication. We overcame some of the cons of our simple authentication protocol using public-key cryptography, but two key challenges that are inherent to the use of PUFs remained. Using these challenges as motivation, we briefly described how fuzzy extractors can be used as a vital tool to create reproducible secret keys from PUF fingerprints in any security context.
Additional resources
Whitepaper
Hardware Root of Trust: QDID PUF & Attopsemi OTP
This whitepaper presents a simplified, secure, and ready-to-use root-of-trust solution for embedded devices by integrating Attopsemi’s I-fuse technology…
Read more
Whitepaper
QuarkLink for Industrial PCs
This white paper introduces how Crypto Quantique’s QuarkLink SaaS device security platform is used with industrial PCs running Linux.
Read more
Whitepaper
What is secure provisioning of an IoT device and why is it important?
This is a white paper on secure IoT device provisioning, and why it is important.
Download

